We’re navigating in waters where customer data is under attack from hackers and bad actors and increasingly we’re being pushed to a situation where we have zero trust, nothing new there you might say, however when we read and hear about the nature of these attacks and some of the targets that they pursue, we collectively need to recognise that the fewer opportunities there are for exposing confidential and sensitive data, the better.
The landscape where customer data is housed is under constant threat from hackers and malicious actors, and where there’s a push towards a zero-trust environment, can indeed be challenging. Here are some thoughts, ideas and strategies that you might want to consider in order to address these existing and growing challenges.
Navigating an Era of Zero Trust with Pretectum CMDM
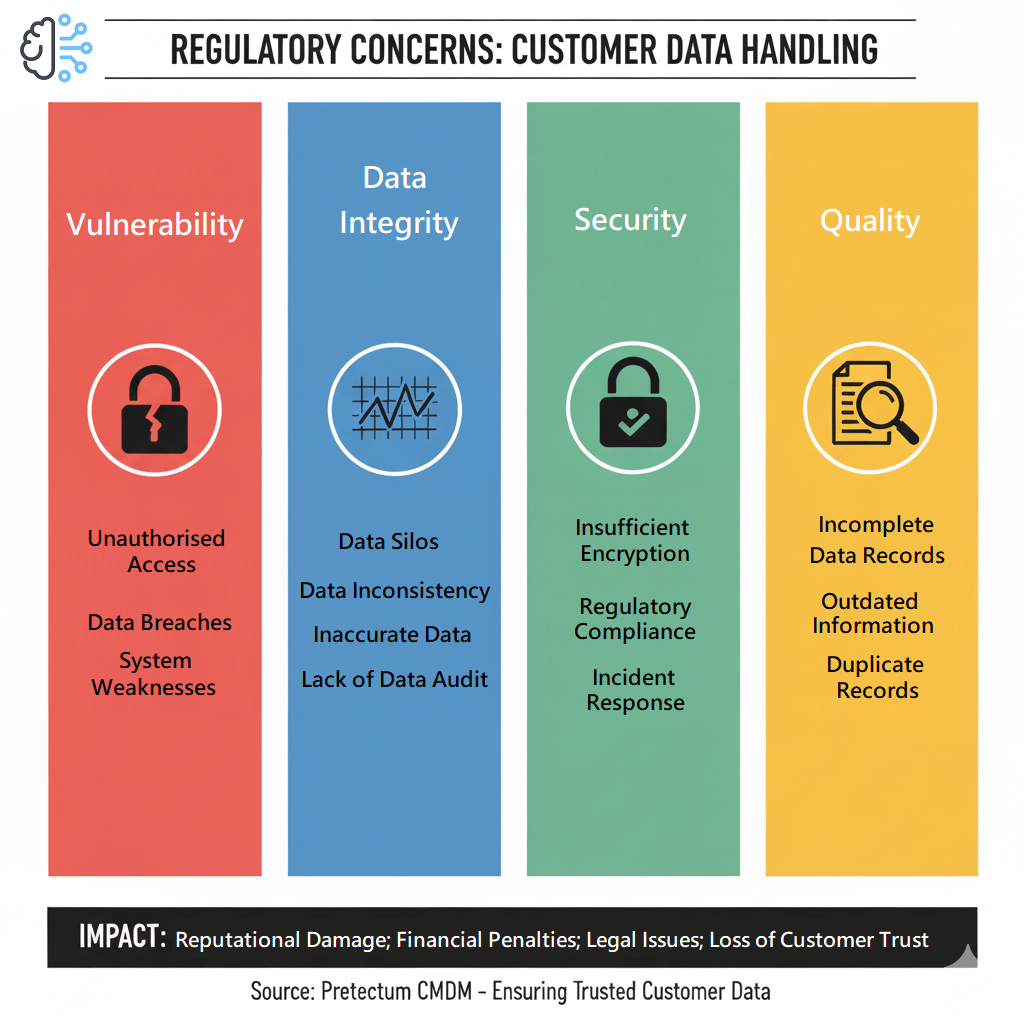
Modern approaches to customer data management mean that trust should not be assumed— trust must be continuously verified. As the news bears witness, all kinds of organizations face escalating threats from cyberattacks, data breaches, and regulatory pressures, making traditional perimeter-based security models obsolete.
A Zero Trust Architecture (ZTA), is a paradigm shift that assumes no entity—whether inside or outside the network—should be inherently trusted, employees for example, are often victims themselves or simply careless. For any organization managing people master data, this zero trust approach is not just a best practice but a necessity.
Pretectum’s Customer Master Data Management (CMDM) platform is built from the ground up adhering to Zero Trust principles, and ensuring that every role based access control, data unmasking, and data transaction, and integration point is authenticated and authorized. Unlike some legacy systems that might rely on credentials with broad access permissions, Pretectum CMDM enforces a model of least-privilege access, this means that there is dynamic policy enforcement, and continuous monitoring through event audit and logging. This is particularly critical in a federated hub-and-spoke model of use, where business units across different jurisdictions manage customer data with varying compliance requirements.
Security by Design: Encryption, Classification, Roles, Masking, Auditing and Logging
A Zero Trust framework is only as strong as its underlying security mechanisms and how effectively these are configured. Pretectum CMDM employs some of the highest available encryption techniques for SaaS platforms, this ensures the housed data is protected both at rest and in transit. Irrespective of whether the data is stored in a multi-tenant cloud environment or exchanged between integrated systems, customer data remains necessarily shielded from unauthorized exposure.
Beyond encryption, data classification itself plays a pivotal role in identifying and securing sensitive data. By analyzing data patterns, the system can assist with determining additional measures that might be appropriate to further secure data and data interactions. Such a proactive stance promotes better customer data governance and respect for the privacy and rights of consumers.
Role-Based Access Controls (RBAC) ensures only authorized personnel have access to specific data and functionality, this follows the “never trust, always verify” principle fundamental to Zero Trust.
Multi-Factor Authentication (MFA) is another option on offer to establish a robust customer data governance posture. Rather than relying solely on passwords which can frequently be compromised adding MFA adds another layer of verification, via magic one time use emailed links or one-time authentication codes, these can drastically reduce the risk of unauthorized access.
Comprehensive Auditing and Logging through the maintenance of detailed audit trails to support the interactive analysis and monitoring of all access events and data changes to customer profiles in support of the concept of continuous verification of user activities.
These are just some of the security measures that help organizations to maintain customer data risk compliance and adherence to data protection regulations all the while safeguarding customer master data against unauthorized access, breaches, and cyber threats.
Minimizing Risk Through Data Governance and Continuous Vigilance
One of the most effective ways to mitigate risk is by limiting data exposure and as such, Pretectum also advocates for appropriate data minimization and masking, ensuring that only the necessary customer attributes are stored and displayed. For example, a customer service agent may only see a masked version of some customer data attribute, while the full details remain encrypted and accessible only to authorized users and systems.
Security is not a one-time effort but an ongoing discipline. In stark contrast to homegrown MDM solutions, SaaS solutions require regular audit and security testing as opposed to more sporadic, underfunded, or overlooked entirely security considerations for in-house solutions.
Human error remains one of the biggest security risks, which is why, even with a great system with controls, employee training and awareness is essential. While some organizations struggle to implement effective training programs, Pretectum’s intuitive design and security features simplify and support security best practices in the platform itself, making it easily deployable and able to be leveraged with commercial training solutions.
Preparing for the Inevitable: Incident Response and Privacy by Design
Despite all of this, you must prepare for the risk of breaches. Having a robust incident response and recovery plan is critical for business continuity and to respond to regulator and customer questions. Many homegrown systems lack the infrastructure to quickly respond to, contain, and remediate security incident issues. Pretectum CMDM, as a managed service, provides higher degrees of assurance, from entire platform locking to comprehensive auditing content available for analysis. This ensures you are able to take rapid action to minimize damage and maintain compliance with breach notification laws.
Privacy by Design is embedded in Pretectum’s architecture. Rather than treating privacy as an afterthought, the platform helps to ensure compliance with various privacy and consumer data handling regulations from the outset. This includes features like self-service data curation for consumers and consent management, where customers explicitly grant or revoke permission for data usage—a necessity in an era of zero-party and first-party data strategies.
Collaboration and Transparency: Building Trust with you and your customers, as a partner
Security is not a solo endeavor and as such Pretectum is in it with you, to actively collaborate on staying ahead of emerging threats and evolving compliance standards. When you choose a modern, cloud-native CMDM solution your organization benefit from shared intelligence and collective security advancements rather than bearing the burden alone.
Equally important is customer education and transparency, consumers demand control over their data, and Pretectum’s consumer data self-service support empowers them to view, update, and manage their preferences. This not only enhances trust but also improves data accuracy—reducing the risk of stale or incorrect records being used.
For businesses at any stage of organizational maturity, adopting Pretectum means future-proofing customer data management. Whether deploying a centralized hub or a federated model for regional business units, the platform provides the flexibility to align with local regulations while maintaining global governance standards.
Embrace Zero Trust with Pretectum CMDM
The era of implicit trust is over. Cyber threats are evolving, regulations are tightening, and customers expect greater transparency. Organizations that cling to outdated data management practices risk not only breaches but also lost customer confidence and regulatory penalties.
Pretectum CMDM offers a modern, secure, and scalable solution—built on Zero Trust principles—to navigate these challenges confidently. By leveraging advanced encryption, comprehensive logging and privacy-centric design, businesses can protect their most valuable asset: customer data.
The question is no longer if you should adopt a Zero Trust approach, but how quickly you can implement it. With Pretectum, the transition is seamless. Don’t wait for a breach to act—secure your customer master data today.
#LoyaltyIsUpForGrabs


