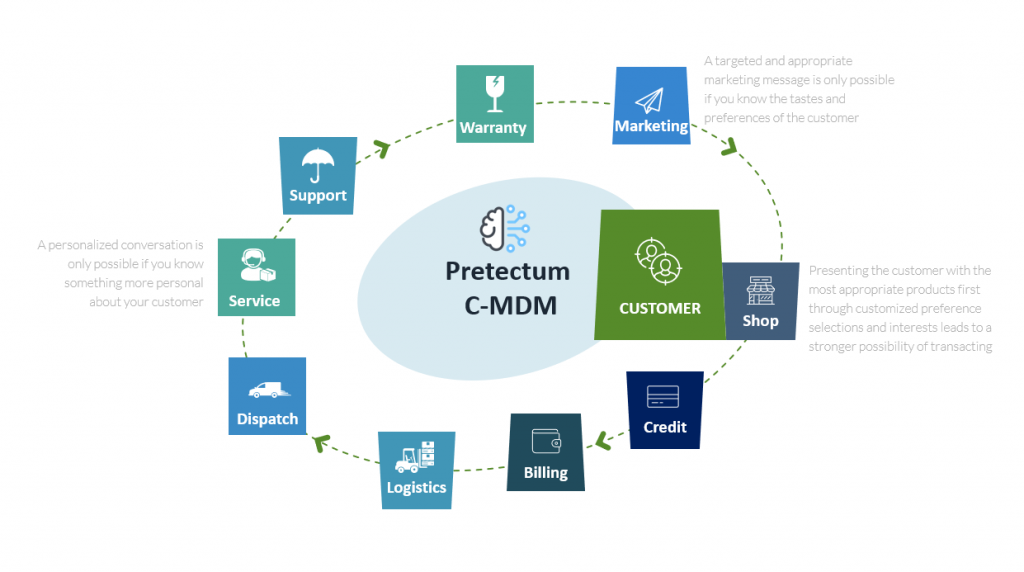
We’ve talked in the past about the importance of your organizational brand and how you can leverage data to improve your brand, get closer to your customer through personalization of their experience and through refining your communications and messaging.
An important facet of all this is of course ensuring that you have the right data and the most appropriate data, not too much, not too little. Most important though is ensuring that you have the rights and permission to use the data, ideally directly through consented use. But, there is another aspect to all this that is just as important, and that is the question of data security assurance.
The press has often called out how there have been data breaches, data leaks and proliferation of hacked data put out on the internet for bad players to use either to impersonate consumers or to steal money or personal information. The imagination and creativity of the criminal underworld seem boundless with even a number of hacker-types simply messing with systems and data records to be subversive. You can think of it as a kind of data and system vandalism. Initially, it seemed trifling, then it became malicious – measures were put in place to remediate by various actors and now when it happens it is simply downright annoying for many of us. There is no end in sight.
When it comes to how your organization gathers and manages customer data this is a major potential headache. Many countries now have comprehensive data privacy regulations in place and quite apart from the pressure on your organization to ensure that you have the appropriate consent, you now have the added obligation of ensuring that the data that you have is well secured.
Industry standards around the securing and encryption of credit cards have been a mandate from the credit card industry since the early noughties but to date, there isn’t a generally accepted policy much less a regulation or standard for securing personally identifiable or sensitive data in general.
Most regulations relate to data breaches and how you should or could handle data in the normal course of business but no one is telling you that data should be housed in a particular kind of system with a particular kind of encryption, with a particular kind of access control etc.
pretectum tasks that whole matter of securely managing your customer data very seriously. We do this because we recognise that cloud applications pretty much serve up particular functionality but don’t allow the users of those systems to do much more than feeding those systems and retrieving data from them. The approach to securing the data is governed organizationally by what permissions you might assign to your users but the rest is left to the SaaS vendor to manage and control.
Just as with any business-critical business solution, the proper collection and management of data are essential for ensuring data quality and minimizing the likelihood of data breach issues. Data breaches, in particular, result in a loss of customer confidence and trust in your brand and business reputation – it’s a reliability issue too.
At its core, management of the customer data that you have has a strong focus on ethical collection, secure storage and appropriate management of the customer information. You’re doing this for the purpose of optimizing your customers’ experience and improving your overall offerings, service and support. Doing this well is a fundamental characteristic of effective customer data management.
You’ll know you’re effective in this area of your business when you see increased customer acquisition, improved cross and upsell; improved customer retention and reduced churn; higher overall customer lifetime value and sustained customer loyalty.
Divisionally, it is evidenced in better marketing outreach yields, higher customer satisfaction and net promoter scores and the growth of market share in sales.
Some aspects of best-in-class data management practice and in the particular curatorship of customer master data focus on the what and others on the how. Pretectum likes to support customers in focusing on the what rather than the how given the fact that Pretectum customers are using shared infrastructure with one another in the Pretectum CMDM platform.
If you’re using some other platform for customer master data management, you might choose to focus on the how, but you will still need to come back to the what at some point.
Here are the ‘whats’ that we think matter.
Invest in data security
According to the 2018 “Cost of a Data Breach Study” conducted by Ponemon Institute for IBM, the average cost of a data breach is $3.86 million. For a company with 50,000 records a data breach could cost them as much as $120,000.
Gather customer data ethically
You might have heard about the Cambridge Analytica scandal with Facebook data, the general public was outraged and the revelations ultimately led to a large number of consumers deciding to change the way that they think about and use social media platforms.
Focus on only the data you need
It is likely that your customer master data is used by a wide-ranging group of stakeholders from marketing through, sales service and support. If you sell on credit then your accounting team likely needs access too. IDC research suggests that as little as 5% of all data held is actually needed and analyzed. Ensuring that teams have access to only what they need is key. Ensuring that you have only the barest minimum of data necessary to meet the needs of the customer is the second piece of the puzzle. Figure out and decide access controls and work out the minimum data you need for your organization to function effectively.
Maintain data quality
Customer data deteriorates at an astonishing rate- perhaps even as quickly as 5% per annum. Customer data can therefore quickly become outdated. Customer database inaccuracy affects effectivity of marketing campaigns and erodes collections recovery. In addition, communicating with customers using old or bad data leads to a potential loss of customer confidence in your record keeping. Analyze your customer data regularly and clean it up as required.
Pretectum’s customer master data management CMDM platform has robust permissions-based security that requires all users to authenticate to access the system, whether they are using the UI or APIs.
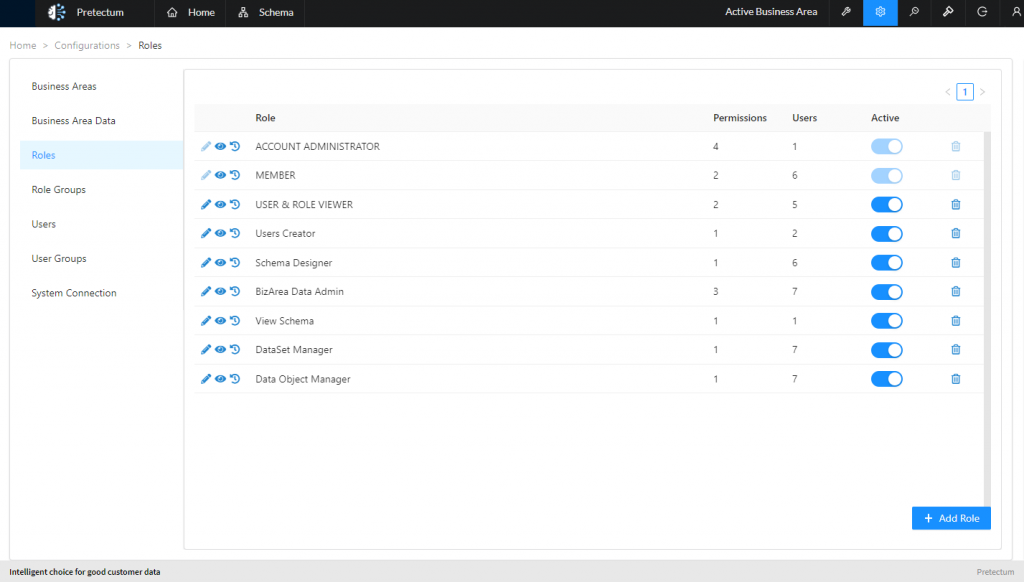
Once within the system users have access to only those areas of the system that they’re assigned access to and only to the data that they themselves own or they have been given access to. Data is encrypted at rest and communications with the system are only permitted through secure data exchange mechanisms.
Data Quality is baked into the processes supported for Pretectum’s data management. If you set up data validation around certain data, the system ensures that you capture and store only data that conforms.
You’re warned all the way through the process of data collection and management about data that is faulty or problematic.
Contact us to learn more.


